A short introduction to technology and application.
Radio Frequency Identification
- Silicon chip for storing data
- Contactless data transmission between reader and tag (wear-free)
- Tags (mostly) without their own energy source
- Direct contact between the transmitter and the receiver is no longer necessary

RFID technology: there is no such thing as the RFID tag
- Important differentiating criteria:
- Active and passive tags
- 1.) Ranges and coupling types:
- 2.) Close coupling up to approx. 1cm
- 3.) Remote coupling up to approx. 1.5 m
- Long range up to approx. 10 meters passive, active approx. 100 m
- Transmission speeds: 20 times faster than barcodes
- Storage capacities
- Anti-collision procedure
- Encryption / cryptographic procedures

Principle of data transmission with a passive tag
Figure: Principle of data transmission with passive label / tag

Basic functionality of RF identification

Classic RFID tracking
- Reader gates are strategically positioned. “The world” must be known
- Central server collects tracking information about the locks (communication network
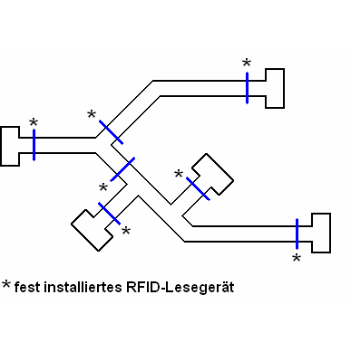
- stationary reading devices for incoming goods

- Stationary reading devices for incoming goods via conveyor system

"Mobile RFID tracking"
- We assume that the position change of the objects to be tracked (mostly) takes place through the carrier of the reader
- “The world” may also be unknown beforehand within certain limits

- Schematic structure of the mobile reader
"Distributed mobile RFID tracking"
Multiple mobile readers
When reading device encounters, “RFID tag sightings” are mutually updated
The more reading device carriers, the more up-to-date and more accurate the tracking data ("external movements" are better recognized or can be directly evaluated and alarmed)
Anti-collision strategies
1. „Slotted ALOHA“
- Several response slots, each with an address length
- Every tag within reach selects one of the slots at random
- Detected tags are muted
- Fast (but only within reach for very few tags)
2. „Binary search tree“
- Bit-accurate collision detection
- Address bit masks
- Detected tags are muted
- Slower (but always works)
Security issue
- Lack of anonymity, as tag ID = tag address
- Eavesdropping on the communication between the reader and the RFID tag is possible with most systems, since encryption requires a relatively large amount of electrical energy

- The "repeater attack" - general attack on the "authentication by possession" method

Use cases
Primary areas of application (tracking & process tracing)
- Logistics in trade, industry and services
- Monitoring of goods and objects (people etc.)
- Identification of goods and objects
- Position determination, access etc.
Contactless acquisition of data without direct visual contact
Electronic programming and storage of data
Robustness of the transponder (up to 1,000 ° C, under water, etc.)
Bulk acquisition (large number of transponders in one step, also called batch acquisition)
Basic structure IoT & IoS
- Digital flow of goods with central storage of information
-
Communication and processing of data
-
Identification of the objects using RFID tags
Use case questions
- What does it look like or do the use cases look like?
- What should be achieved / what is “the big goal”?
- In which phases should what be achieved?
- Quantities and masses to be considered?
- What else is there to consider?
- What are your wishes for such a project?
- Success: what should be measured so that a success / failure can be determined?
- Structure of a PoC / frame?
- Time horizon / schedule?
Perhaps also interestingt: